People can work remotely on a number of different devices, which can make it difficult for business leaders to manage where their information is being sent and used. As more companies learn how to work from home effectively, mobile device management becomes a clear concern for business owners.
Microsoft Intune is part of the company’s Modern Office suite—and it’s the perfect platform for mobile device management (MDM) and mobile application management (MAM). In this guide, our experts are going to take you through Intune’s features and benefits to show you why you should be using the platform to manage your business-related devices as you and your employees work from home.
What Features Does Microsoft Intune Have?
Intune is Microsoft’s cloud-based service used for mobile device management (MDM) and mobile application management (MAM). Intune is part of Microsoft’s Enterprise Mobility and Security (EMS) suite. It empowers users to be productive while keeping your organization’s data protected.
Intune also integrates with services like Microsoft 365 and Azure Active Directory (Azure AD) to control user access and utilize Azure Information Protection. When you use Intune with Microsoft 365, you allow employees to be productive on all their devices without sacrificing your business’s information.
Let’s take a look at some of Microsoft Intune’s key features to break down exactly what all that means.

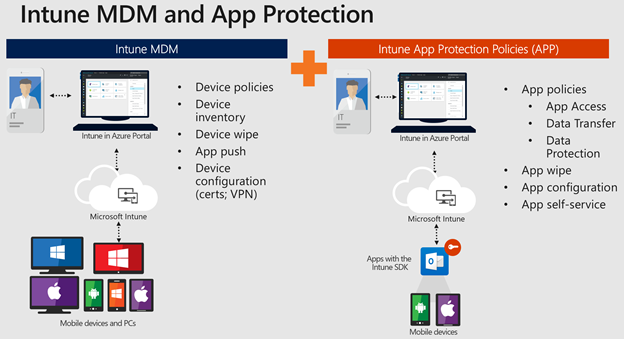
Mobile Device Management (MDM)
Intune offers two different options for device management: organization-owned devices and personal/bring-your-own devices (BYOD).
If your employees are equipped with organization-owned devices, Intune allows you to have complete control. This means you regulate how much employees can modify the device’s settings, features, and security measures. To do this, your employees enroll in Intune, essentially signing themselves up for full access to the device’s features (with whatever restrictions or limitations you’ve put in place). Enrolled employees receive those settings through policies configured in Intune.
When it comes to personal devices, employees might not want you to have total control. Luckily, Intune has options for you to manage certain aspects of their devices to ensure sustained security and productivity while working remotely. Employees can still opt in and enroll for complete feature usage. However, if they only want to use a few specific programs (like Office 365 and Microsoft Teams), you can implement protection policies like multi-factor authentication (MFA) to maintain cybersecurity.
Here are a few key takeaways of what you can do if your employees enroll their devices to be managed using Intune:
- Monitor enrolled devices and see which devices access your organization’s resources.
- Specify device settings so they meet your security standards.
- Push certificates so users can access your Wi-Fi network or use a VPN to stay connected.
- Get reports on users and devices that are compliant or not compliant with your settings and standards.
- Gain the ability to remove your business’s data if an employee’s device is lost, stolen, or no longer in use.
Mobile Application Management (MAM)
Similar to MDM, applications can be managed on an organizational or personal level.
Here are some key features for apps managed using Intune:
- Create and assign mobile apps to specific user and device groups.
- Set up configurations so certain apps start or run with specific settings enabled, as well as update apps on employee devices.
- Get reports on apps being used and see analytics on their usage.
- Maintain security by removing your organization’s data from managed apps.
Intune also provides mobile app security through the use of app-protection policies. Let’s break down what that means.
- Use Azure AD to separate your organization’s data from employees’ personal data. This means data accessed using organization login credentials has heightened protection.
- Maintain security on personal devices by restricting user actions (like copy and paste).
- Policies can be created and deployed on almost any device, whether they are enrolled in Intune or not. App-protection policies add an extra layer of protection to enrolled devices.
How Does Intune Benefit Your Business?
Businesses all over the world are trying to figure out how to work from home while keeping up with the latest cybersecurity trends. The Microsoft Modern Office suite has the features and capabilities to make that transition a little easier—and Intune plays a large part in this change.
Intune allows you to simplify modern workplace management and achieve digital transformation while creating the most productive Microsoft 365 environment for users. With Intune, employees can work on the devices and apps they choose—and protect your business’s data.
As a business owner, Intune allows you to manage your employees’ work-related mobile devices and applications with ease. Cybersecurity is a top concern when working from home and Microsoft Intune can help you promote safety without sacrificing efficiency or productivity.

How Can WheelHouse IT Help Your Business Get Started With Intune?
Here at WheelHouse IT, we want to make sure your business continues to succeed in these uncertain times (and beyond). We have a dedicated and experienced team of managed IT professionals who can help you navigate this new way of working and assist you in implementing Microsoft Modern Office and Intune for your business.
Work with a team that is knowledgeable and has experience with Modern Office by getting in touch with us today. Intune has the features needed to effectively track, manage, and secure your business as it continues to work remotely—and WheelHouse IT has the experts to help you implement it effectively while maintaining the latest cybersecurity trends.
Let’s work together to make sure your business remains as effective, productive, and secure as possible.











